Significance of Identity and Privacy is the first article of a trilogy on privacy for small businesses, a series by Irene Silberstein. This article discusses the semantic, practical and legal angles.
I wrote this series for businesses with an online presence and websites' owners: small and medium companies, retail, expert, freelancer, creator, publisher, adviser, agencies, artist and many more.
My research on the evolution of privacy started quite a long time ago, but restarted recently while researching a cosy and friendly way to access our topical websites.
This research ended at the crossroad of semantics(1), common sense and business practices.
At the heart of the privacy debate, I question the significance of the words identity and privacy for ourselves and our clients.
Updated May 2024.
Note 1.
a- noun - The science of meaning (the sense carried by a word or expression)
b- adj - related to the meaning
Average reading time: 17 minutes.
No time to read now? No problem, email us at [email protected] to receive the PDF version (copy paste [email protected] in the to field of your email).
Should a provider require the ID of a client? 
Although I can imagine this requirement in some specific cases, my common sense refuses the idea that a grower selling potatoes online should have to control the ID of its customers.
Indeed, It hurts my common sense. Not yours?
This observation triggered a questioning about the data we truly need to render our service.
Looking at selling marketing services for instance, we possibly need to know if our client has a website, participates in commercial fairs, sell worldwide or locally. Yes, but why should we need to lean about the date of birth of its Head of sales?
So, the first question that comes to my mind is
Does selling online require to control identities?
I hear some of you say "but secure bodies provide proof of identity..."
Sure, but even done by a third-party it is still an ID control.
Another question:
 Do we have the right to exercise this control?
Do we have the right to exercise this control?
Possibly no. In many countries, ID controls are strictly regulated and entrusted to Customs' agents and Police forces. Website's owners confronted to such requirement might commit a criminal offence.
Oh yes, but if you sell medicines and one cannot be sold for a child under 12 years, they have to!
Well, when selling 10,000 products and having 2 that cannot be sold to under-12 in this precise case, you should either not sell the 2 under-12 products online or talk to the person who wants to order. It is meaningless to build a general rule from an exception; and if you sell many forbidden under 12 products, then set up a phone service for this type of sales.
Yes, words matter 
Semantic shifts plant the seeds for wrong ideas.
In our society, semantic shifts are so common that we hardly notice them. We enter a trap and use a word instead of another.
Today's use of the expressions identity/identification is one of these traps.
Have a look at it: a system authenticates a user to allow access and check its rights.
Examples:
Unix OS system came first, before Dos and before Windows that inherited a part of the Unix logic.
To access a Unix or Linux system a user needs the proper credentials.
The user ROOT gets all the rights (for instance all rights, that comprise delete)
The user ADMIN gets admin rights (for instance all actions that can be reversed)
and user JOE gets some rights
No need for the system to learn or store the real name of root nor in this example the date of birth of joe.
In such a case, to design a secure system we shall simply decide what the proper credentials are, not more.
Today's practices

To allow access to a collaborative platform for instance
the platform frequently requires an identity provider.
It confuses me, not you?
Indeed, IT concepts, possibly meaningful for experts and developers
may become a source of confusion when used by marketers or politicians.
It wouldn't confuse us if called authentify instead;
Indeed, from here we can track the semantic shift.
Think about it: all of this supposedly to secure the user and its data.
Shall we believe it? Certainly NO.
This is simply a wrong statement. As you will see further, GDPR history and statistics give evidence of it.
Not only it does not bring any security, but it frequently becomes a nightmare for the user.
 A brief historical reminder
A brief historical reminder
From ca 2008, security consultants began to explain their clients' target in their commercial papers that "ID verification" and ID authentication" were distinct concepts, the first (ID verification) implying only to present an ID while website's owners would have to add an extra step to protect from fraud, especially for online sales.
In the next decade, the idea of an ID provider found its way and large well-known corporations such as Google, Facebook, etc. became the warrant of the users' "identity". They began to offer the service, so that website's owners could offer single sign-on to their users. At first, it seemed cosy to the users.
Research for the most part targeted protocols, procedures, secure processes, performance. However, the foundation was not at stake.
"Proof of identity" entered the play. Roughly said, I understand the concept of proof as layers and layers of identification and verification added.
Since 2012, various papers showcase the 'risk' of fraud and the need for identity proofing, with many showing a clear commercial interest.
Since 2017, the wording "identification vs authentication" got attention.
Marketing managers argued that ID frauds and threats were on the rise.
Let's have a look at this.
Breaches, phishing, and more
Sellers and marketers argued of increased data breaches claiming seven digits figures and calling for increased user access control. They didn't question the reasons for this increase in breaches.
Stop. The facts collected might demonstrate that the identify mania could be a main cause of breaches.
Indeed, for the US alone, the number of data breaches jumped
from 784 in 2015 to 1106 in 2016 (2) and 1632 in 2017
Note 2. The year GDPR was born
then 1257 in 2018, 1473 in 2019 to decrease to 1001 in 2020(3)
Note 3. The year the EU Court of Justice demolished the GDPR trick
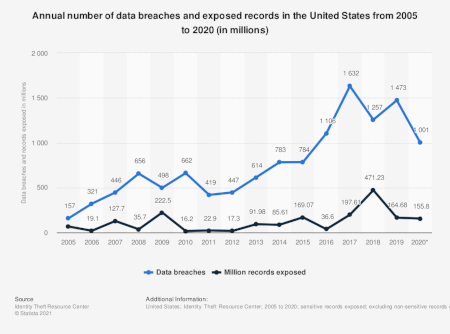
Source Statista 2021
So, the nice speeches about fraud increase and the need for increased verification collapse.
Worldwide Legal Landscape 
A quick look into GDPR
What happened? From August 2016, the EU-US Privacy Shield framework allowed to subcontract to companies invoking the US privacy shield - a simple declaration.
Sure, this was at the opposite of the former rules in European countries.
So if you thought that GDPR was an advance in privacy, forget it. GDPR opened the door to breaches, caused a regression of personal data protection and created a legal jungle.
Why? Because, at the request of the US Department of Trade, the EU acknowledged to transfer personal data outside the EU.
And the result was that, despite a jungle of legal measures, no longer any control existed on subcontractors, opening the door to breaches.
In 2020, the CJEU Court Ruling
The Court rejected in August 2020 subcontracting outside the EU.
One month later, there were over 100 complaints filed against websites for continuing to send data to the US via Google Analytics or Facebook, by the European privacy campaign group Noyb..
But you will say, how does this relate to me?
From website's owners, the EU law requires that you know what data you capture, where you store these data, how you protect them and who owns the data.
Complicated and hard to comply with.
A simple example: Google, Facebook and others own the software, manage the users' data and identifies them (not always as a natural person but as a distinct entity). This is why using their products you become unable to comply.
See how it works?
In the EU for instance, businesses transferring personal data to the USA, especially when the subcontractor uses cloud-based services, must now switch immediately to service providers based in the European Union or a country that can ensure an adequate level of data protection.
A recent phenomenon
--Due to local privacy regulations, lack of sound privacy, failing to properly manage cookies or to declare customers' data, or other non-compliance can lead to a fine in many countries, not only in the EU.
Apart from EEA countries, businesses operating at international level or receiving visitors from other countries need to respect privacy laws as well.
Look, as of 28/01/2021, Morrison Foester indicates
"The number of data privacy laws around the world has skyrocketed in recent years. As of January 2021, 133 jurisdictions around the world have enacted omnibus data privacy laws; 102 of those laws [1] are in jurisdictions outside the European Economic Area (EEA). [2] With sixty of these laws enacted in the past 10 years and half of those within the past five years. In the next couple of years alone, we may see as many as 12 or more new or updated laws enacted or introduced into national legislatures."
Switzerland, Japan, Florida, Canada, but as well India (Indian jurisprudence recognized privacy as a constitutional right), Singapore and now China PIPL (the Chinese Personal Information Protection Law requires compliance from 1st November 2021. As with the GDPR, the PIPL impacts any company with data in China or who does business there.
A complete analysis goes beyond the scope of this article, but the above information might help understand how complicated it is to comply with the regulations.
Many organizations and authors offer views on several facets of privacy as of 2021. Among the problems and solutions some authors see:
DIGITAL DATA AND PRIVACY, an article on Medium by Mayank Bhandary 12/07/2021. The author contributes a useful article to discover why our digital privacy is at stake and how we can protect it.
Why Data Privacy Matters to Me, an AdTech Dropout,an article on Medium by Lauren Kaufman, 14 September 2021. As the author, I consider that privacy and ethics shape a fundamental ground for our societies. However, obviously for me we can all contribute building this block.
The Calyx Institute, a Medium publication dedicated to privacy solutions publishes:
Awala - A Light in the Darkness of Internet Blackouts.
By Cathy B. 17 September 2021: An E2E encrypted sneakernet helps users stay connected even when the internet is cut off.
Tor and Snowflakes By Brandon S. 23 August 2021: How You Can Be Part of the Digital Privacy Solution.
 Taking care of privacy
Taking care of privacy
In September 2021, Ireland's data watchdog fined What'sapp, Facebook owned, a record $267 million for misleading users and violating 2020 European Union data privacy rules.
Until then, the record fine was 886.6 million Euro meted out to Amazon by the Luxembourg National Commission for Data Protection (CNPD) privacy agency in July 2021 for processing personal data in violation of the bloc's GDPR rules.
A few months ago, Restore Privacy highlighted that
"In just the last few weeks", we saw "533 million user records stolen from Facebook and another 500 million records stolen from LinkedIn" [owned by Microsoft] in The Ultimate Guide to Private and Anonymous Payment Methods (2)
Restore Privacy rightly observes:
"The problem: you don’t have control over the databases "that stores your private information...
The solution: start using private and/or anonymous payment methods, which minimizes the data available...
Unfortunately, you can't count on companies, or even governments, to protect your personal information..."
Certainly, but as individuals and as business owners, we can help each other, in our common interest.
This is why my own research of simple solutions led to lower and secure the user data collected.
Zero-knowledge from the business angle is a way to lower the burden and the risks.
In the next article of this series, I will investigate with you the risks involved and how to avoid traps.
Sources
Chunk of history sources:
November 2012
October 2016
2017
https://www.experian.com/assets/government/white-papers/identity-proofing.pdf
November 2018
https://simplicable.com/new/identification-vs-authentication
August 2019
https://www.okta.com/blog/2019/08/what-is-identity-proofing/
December 2019
February 2020
https://www.jumio.com/identification-authentication-verification-compared/
May 2020
https://docs.microsoft.com/en-us/azure/active-directory/develop/authentication-vs-authorization
June 2020
https://searchsecurity.techtarget.com/answer/Authentication-vs-digital-identity-Whats-the-difference
December 2020
https://www.paymentsjournal.com/telling-the-difference-between-identity-and-authentication/
2021
https://www.cnn.com/2021/04/06/tech/facebook-data-leaked-what-to-do/index.html
2021
https://www.aware.com/resources/cloud-based-biometric-identity-proofing-and-authentication-services/
Sources for Data Privacy laws:
Morrison Foerster
https://www.mofo.com/resources/insights/210127-data-privacy-day.html
China's new Personal Information Protection Law
https://www.wrangu.com/solutions/data-privacy-management/
Other sources for privacy
https://legal-nen.medium.com/digital-data-and-privacy-c2aa2e023cfb
https://lolokaufman.medium.com/why-data-privacy-matters-to-me-an-adtech-dropout-b7b126a0c8aa
https://medium.com/@calyxinsta/awala-a-light-in-the-darkness-of-internet-blackouts-f6485e59c5d8
About the author
Information specialist and web pioneer, Irene offers an extensive experience in information strategy, research and analysis. She manages Information Strategies Key intangible Value, a UK limited company, to learn more, see Irene Silberstein